(SECURITY) The Cloud
The 50 Biggest Data Breaches
 As companies rush to move their data to The Cloud, and to be Serverless; their data is being aggregated into fewer and fewer organizations. What follows are some points to consider before doing so and an appeal to factor in the possible long-term costs of moving to the large cloud vendors.
As companies rush to move their data to The Cloud, and to be Serverless; their data is being aggregated into fewer and fewer organizations. What follows are some points to consider before doing so and an appeal to factor in the possible long-term costs of moving to the large cloud vendors.
First off, in no way will your data actually be serverless. "Severless" is simply a marketing phrase used by the cloud companies; rather, your data is now just on someone else's server -- and is no longer under your direct control.
In some cases you do not even control which other companies (lets call them "the partners" of the cloud company) will now have access to your data. As part of the contract terms you may have been required to accept having these partners help to manage your data.
Going "serverless" with the big cloud companies may save your company dollars in admin time and infrastructure today; but it is not unlike U.S. companies saving money by outsourcing manufacturing to China. You may save money today; but what is the cost in the long term, if those manufacturing plants are nationalized? Or even just shut down for an extended period by pandemic or war?
The same sorts of give-and-take applies to cloud computing. What will you do if your cloud vendor is taken offline by a hack? Or network outage? Or a government kill-switch?
Will it even be possible to decouple your code/data from the cloud approach if you ever need to?
But, the most important question is: What is the cost to your business if your customer data is compromised en masse?
Either now, or in the not-to-distant future, when some distraught cloud employee decides to leak data; or a hacker defeats the cloud's security; or just if a government decides they want to see it that day; your data will be compromised.
The tricks used to defeat cloud security are becoming more advanced. For one example, consider "Cloud Squatting":
Yes, something like Cloud Squatting can be used against a server in your own facility. But when placing data into the large cloud vendor servers; many economies of scale are presented to the hackers. If they learn to defeat cloud security to get at one companies' data; they largely have done so for many other companies data at the same time.
Similarly, if the cloud vendor itself experiences a system wide problem (e.g. Amazon AWS outage) then many companies are hit at the same time. Carrying this same issue forward to the trend of "canceling" companies -- if a government/entity/group decides to ever block, say, AWS, they can do so much more effectively than if the same government/entity/group had to block tens of thousands of individual servers.
Just to show that data is being breached; and breached a lot, consider this graphic of the 50 largest data breaches so far:
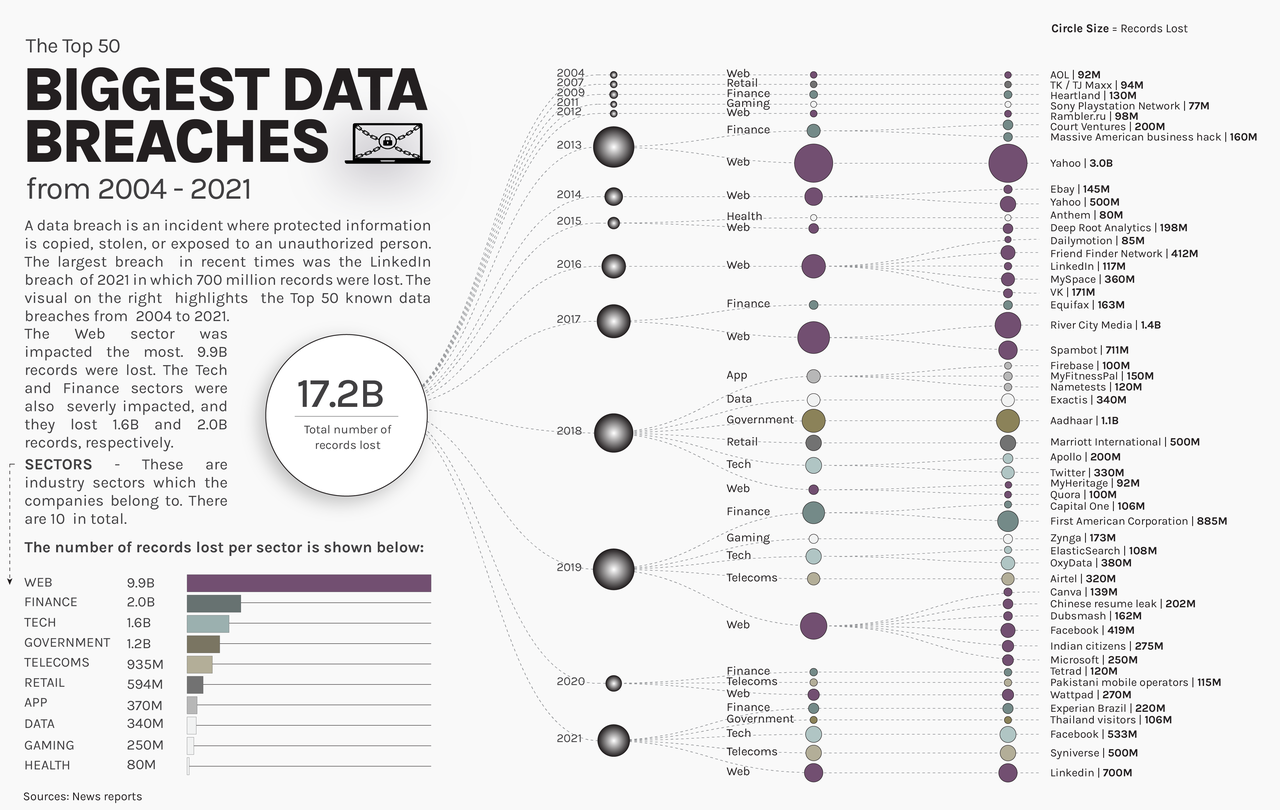
source: ZeroHedge
The companies on the list include some of the largest ones, like Microsoft (250M records breached), Facebook (419M) and Yahoo (3.0B). Yes, that was B as in BILLION. Heck, Yahoo even makes the biggest list twice, with another breach of 500M on there. Ditto with Microsoft ... as they own LinkedIn.
Remember, these are only the 50 largest breaches. There are thousands more.
And many of the same companies shown have been breached other times as well.
The point is, big companies are not safe from this.
Hiding Breaches
Another issue is that large companies sometimes hide the fact that a breach occurred. Perhaps they want to save the hit on stock price that results. Or they may be looking for time to close the hole that was breached, before announcing it.
The real problem here is that while the cloud company twiddles around hiding the breach, the hackers are not waiting for them to disclose it before exploiting your customer data. The damage to the customers is much worse if a company tries to hide a breach. Yet they still do.
Our Recommendation
Force consideration of the long term, when considering a move to the cloud. Include the long term in disaster planning as well. Consider the possible future costs of having to re-buy servers (and administrators) in the cost equations.
And just like your home or office desktop computer, have a backup. Maybe ... like those good old in-house servers that got you to this point. Test the in-house backups periodically!
Don't forget to evaluate how (and how much it would cost) to pull your cloud data and all of your code that will be wired into cloud functions back in-house, if you ever need to. These costs go into the disaster plan too.
